Attack simulation exercises are used to simulate realistic end-to-end Advanced Persistent Threat (APT) attacks against an organization. They should give insights into the attack surface an attacker has and how resistant security controls are against a coherent cyber attack. The simulation usually includes different teams working against or with each other. On one side there is the offensive team which tries to break into the environment. On the other side is the defending team trying to detect and prevent a successful attack.
In this post we introduce our general approach to Attack Simulations and place the foundation for further posts. Today, we answer who the players are, what the cyber kill chain is and describe phases of the attack and kill chain.
Players & Teams
In an attack simulation we have different players who can work together, against each other or in conjunction. One player is the team attacking the organization, which is often called the „Red Team„. The attacking team may be juxtaposed by a defense team („Blue Team„) during the exercise. Member of the Blue Team are usually not aware that a targeted attack is happening. To avoid escalation during the simulation, the Blue Team is sometimes observed by control group („White Team„). The control group is placed within the incident escalation process of the organization and is well informed about the ongoing attack.
Selected individuals of the control group are working in key positions who are consulted, if a serious incident is reported. Those key individuals can distinguish between attacks happening at the same time as the attack simulation. Additionally, they are the barrier to avoid escalation to external authorities. This can for example happen at the very end of the exercise to verify if the escalation process would have worked in case the Red Team would have been detected.
The Cyber Kill Chain
Describing the attack path and performed actions during the simulation is an important task. It is needed to inform the White Team during the simulation and also for the aftermath workshops with the Blue Team. At Y-Security we utilize a kill chain to describe our attack path taken during the simulation.
The kill chain is formed out of two frameworks. It includes Lockheed Martin’s kill-chain, which is part of a framework for identification and prevention of cyber intrusions activity. Additionally, it includes the MITRE ATT&CK® framework. The MITRE ATT&CK framework is a curated knowledge base and model for cyber adversary behavior. It is used to describe the behavior of Advanced Persistent Threat (APT) groups and software they use. Describing attackers is performed by aligning them to Tactics, Techniques and Procedures (TTPs). Both, Lockheed Martin’s kill-chain and the MITRE ATT&CK framework, are used to define our phases of an attack. Phases of an attack range from early reconnaissance to reaching the ultimate goal of the simulation and data exfiltration. Our attack plan and approach are formed by the below Cyber Kill Chain to which we assign TTPs from the MITRE ATT&CK framework:
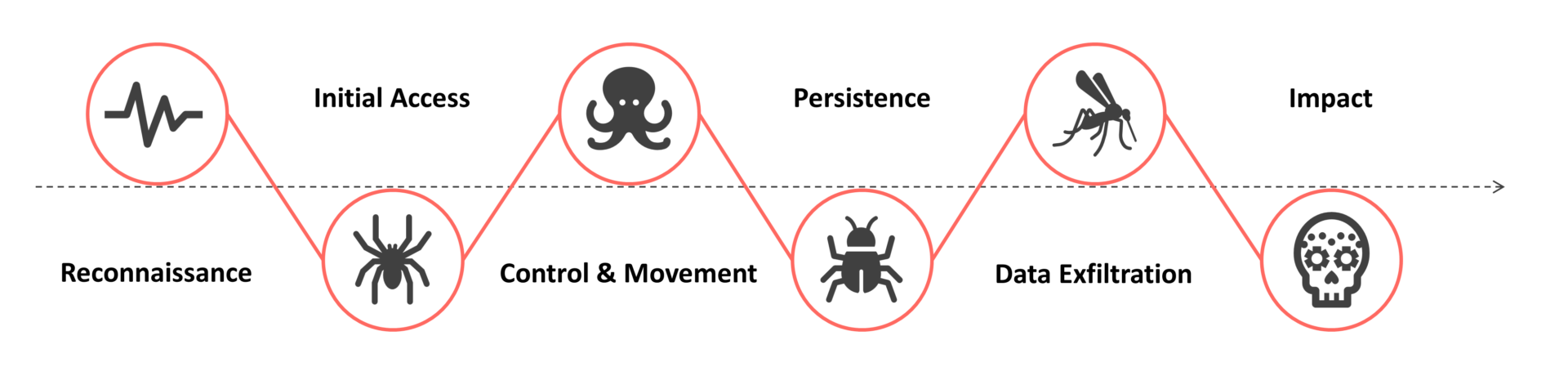
In our Attack Simulations we merged the best of both, Lockheed Martin’s kill-chain and the MITRE ATT&CK framework, into 6 phases. This simplifies the kill chain and provides a holistic and transparent view into our attack plan. Phases of the attack plan are repeatable during and after the assessment to identify key points for the remediation plan. Each phase can have (multiple) Techniques and Tactics assigned to describe our actions performed. For example the Initial Access phase could have the Techniques T1566.001 Phishing: Spearphishing Attachment and T1190 Exploit Public-Facing Application assigned.
Attack Simulation Phases
In the below descriptions we have mapped each phase back to the MITRE Tactics (indicated by TA00XX). Additionally, we have added some basic examples (Techniques) to each phase. We should note that attacks often require higher sophistication level. This includes relaying Two Factor Authentication codes or chaining vulnerabilities into a single coherent attack:
Do your employees list your defense systems as a skill/experience on social media?
Reconnaissance
In most Attack Simulations we have defined a goal for the simulation. The goal can be set to nearly anything like access to a Domain Administrator account or access to a specific server/network segment. A goal can also be physical access to a specific device or room in your premise.
In the Reconnaissance phase of the attack we already have the goal in mind when collecting information. We continue with a deeper collection of data and use gathered information from our Threat Intelligence phase as a base. Overall, the phase aims at collecting information about the target (TA0043). Collected information is also used to prepare the Red Team’s attack environment for further activities (TA0042).
Typical actions performed in this phase include collecting publicly available information from the target’s website and social media. Additionally, we collect details about exposed network services via search engines for Internet-connected devices. Collected information includes technical information about technology in use, but also topics of interest. Those could, for example, be used as part of Phishing campaigns, like an announced company event.
If the attack plan includes physical attacks against premises, then we also start observing your premise and employee’s behavior. This includes observing for „How are they dressed“ and „When/How do they enter the building“.
Collected information is then used to spin up our dynamically extendable environment. We have create a dynamic infrastructure that allows us to create new servers during the simulation and automatically tailor their configuration to what we require.
In most Attack Simulations we have defined a goal for the simulation. The goal can be set to nearly anything like access to a Domain Administrator account or access to a specific server/network segment. A goal can also be physical access to a specific device or room in your premise.
In the Reconnaissance phase of the attack we already have the goal in mind when collecting information. We continue with a deeper collection of data and use gathered information from our Threat Intelligence phase as a base. Overall, the phase aims at collecting information about the target (TA0043). Collected information is also used to prepare the Red Team’s attack environment for further activities (TA0042).
Typical actions performed in this phase include collecting publicly available information from the target’s website and social media. Additionally, we collect details about exposed network services via search engines for Internet-connected devices. Collected information includes technical information about technology in use, but also topics of interest. Those could, for example, be used as part of Phishing campaigns, like an announced company event.
If the attack plan includes physical attacks against premises, then we also start observing your premise and employee’s behavior. This includes observing for „How are they dressed“ and „When/How do they enter the building“.
Collected information is then used to spin up our dynamically extendable environment. We have create a dynamic infrastructure that allows us to create new servers during the simulation and automatically tailor their configuration to what we require.
Initial Access
The Initial Access phase of the attack is used to gain a digital or physical foothold to the target (TA0001). This can be done in multiple ways like by executing code or planting a malicious device/software in the network (TA0002). Actions performed in this phase are one of the most crucial steps. They rely on the previous phase as collected information, such as in-use technology (Antivirus, Endpoint Protection System, Operating System), needs to be evaluated, when building our attack toolkit and preparing exploitation of services.
Typical actions performed in this phase include Phishing (E-Mail, Voice, SMS, Credential) attacks with malicious files which target employees directly. We also exploit external infrastructure components such as web applications or remote access gateways. Sometimes, it is also required to perform physical attacks against the target in the form of Social Engineering attacks. This can also include attacking wireless components such as the corporate network or access control cards.
Initial Access
Phishing via E-Mail is just one way to gain initial access. How often do you perform Voice Phishing & Social Engineering exercises?
The Initial Access phase of the attack is used to gain a digital or physical foothold to the target (TA0001). This can be done in multiple ways like by executing code or planting a malicious device/software in the network (TA0002). Actions performed in this phase are one of the most crucial steps. They rely on the previous phase as collected information, such as in-use technology (Antivirus, Endpoint Protection System, Operating System), needs to be evaluated, when building our attack toolkit and preparing exploitation of services.
Typical actions performed in this phase include Phishing (E-Mail, Voice, SMS, Credential) attacks with malicious files which target employees directly. We also exploit external infrastructure components such as web applications or remote access gateways. Sometimes, it is also required to perform physical attacks against the target in the form of Social Engineering attacks. This can also include attacking wireless components such as the corporate network or access control cards.
Do you have a granular access control on file-shares and document server? Do you use 2 Factor Authentication internally?
| Example Technique | ATT&CK |
|---|---|
| Process Discovery | T1507 |
| Software Discovery | T1518 |
| Data from Local System | T1005 |
| File and Directory Discovery | T1083 |
| Network Share Discovery | T1135 |
| Domain Trust Discovery | T1482 |
| Account Discovery | T1807 |
| Hijack Execution Flow | T1574 |
| Credentials from Password Stores | T1555 |
| Internal Spearphishing | T1534 |
| Lateral Tool Transfer | T1570 |
Control & Movement
Control & Movement is used to collect information about the network (TA0007) to reach the goal of the assessment while moving around (TA0008) in the network.
Actions during this phase include reconnaissance on the target (TA0007) for security controls (TA0005) like listing running processes or reviewing installed software. If additional security software is identified that was not found in the Reconnaissance phase, then we adjust our toolkit and TTPs to circumvent those.
This phase is also one of the most dynamic ones as we learn a lot about the network, components and user/admin behavior in the network. We constantly need to adjust our behavior to become part of the usual flow and not raise any anomalies. For example, if we identify that PowerShell is used in the network, then we adjust our toolkit and payloads to use PowerShell as an executor.
One of the steps on the device is collecting files from the local device or network services like SharePoint and reviewing them on the system itself (TA0009). We also collect general information about the Active Directory like Domain Trust and User/Group access rights to identify overly permissive access. This phase of the attack may take some time depending on the size of the network and information we need to review to further plan our attack. Our insights into Attack Simulations have shown that it is often better to listen for a while.
Additionally, we perform privilege escalation on compromised devices. For example by modifying the execution flow of programs (TA00004). It is often required to move via multiple targets throughout the network. This can for example be archived by privilege escalation within the domain using compromised credentials from a password manager (TA0006). It also not unusual to perform internal phishing campaigns from compromised accounts and hijack existing internal email threads.
Control & Movement
Do you have a granular access control on file-shares and document server? Do you use 2 Factor Authentication internally?
| Example Technique | ATT&CK |
|---|---|
| Process Discovery | T1507 |
| Software Discovery | T1518 |
| Data from Local System | T1005 |
| File and Directory Discovery | T1083 |
| Network Share Discovery | T1135 |
| Domain Trust Discovery | T1482 |
| Account Discovery | T1807 |
| Hijack Execution Flow | T1574 |
| Credentials from Password Stores | T1555 |
| Internal Spearphishing | T1534 |
| Lateral Tool Transfer | T1570 |
Control & Movement is used to collect information about the network (TA0007) to reach the goal of the assessment while moving around (TA0008) in the network.
Actions during this phase include reconnaissance on the target (TA0007) for security controls (TA0005) like listing running processes or reviewing installed software. If additional security software is identified that was not found in the Reconnaissance phase, then we adjust our toolkit and TTPs to circumvent those.
This phase is also one of the most dynamic ones as we learn a lot about the network, components and user/admin behavior in the network. We constantly need to adjust our behavior to become part of the usual flow and not raise any anomalies. For example, if we identify that PowerShell is used in the network, then we adjust our toolkit and payloads to use PowerShell as an executor.
One of the steps on the device is collecting files from the local device or network services like SharePoint and reviewing them on the system itself (TA0009). We also collect general information about the Active Directory like Domain Trust and User/Group access rights to identify overly permissive access. This phase of the attack may take some time depending on the size of the network and information we need to review to further plan our attack. Our insights into Attack Simulations have shown that it is often better to listen for a while.
Additionally, we perform privilege escalation on compromised devices. For example by modifying the execution flow of programs (TA00004). It is often required to move via multiple targets throughout the network. This can for example be archived by privilege escalation within the domain using compromised credentials from a password manager (TA0006). It also not unusual to perform internal phishing campaigns from compromised accounts and hijack existing internal email threads.
Persistence
Persistence is the fourth step of the attack chain in which permanent access to the target is ensured (TA0003). Ensuring persistence is an important, but also critical task as in some cases the configuration of the system needs to be changed. Changing a system’s configuration may be detected by the Blue Team, especially if it is an unusual behavior like the Microsoft Word process creating a new scheduled task.
Permanent access to a system or environment can be ensured in different ways. In some cases, it is possible to successfully compromise clear-text user credentials in the Control & Movement phase or during a Phishing Campaign. Those credentials can then be used to gain persistent access to the network via remote access portals like Citrix or other services. Remaining persistent on an end-user device or server system can usually be archived by different means. This includes adding additional files to the local system, creating new scheduled tasks or by infecting existing files on the system.
Persistence is the fourth step of the attack chain in which permanent access to the target is ensured (TA0003). Ensuring persistence is an important, but also critical task as in some cases the configuration of the system needs to be changed. Changing a system’s configuration may be detected by the Blue Team, especially if it is an unusual behavior like the Microsoft Word process creating a new scheduled task.
Permanent access to a system or environment can be ensured in different ways. In some cases, it is possible to successfully compromise clear-text user credentials in the Control & Movement phase or during a Phishing Campaign. Those credentials can then be used to gain persistent access to the network via remote access portals like Citrix or other services. Remaining persistent on an end-user device or server system can usually be archived by different means. This includes adding additional files to the local system, creating new scheduled tasks or by infecting existing files on the system.
Do you inspect SSL encrypted traffic and monitor DNS traffic?
Data Exfiltration
Data Exfiltration describes the way we communicate with our Command & Control Server (TA0011). It also describes general data exfiltration out of the network, such as the goal (e.g. a dummy database) set in the assessment (TA0010).
Communication with the Command & Control server is done in various ways. This includes standard protocols such as HTTP and more bespoke protocols, if we identify that they are in use by our target. For example, if we identify that Microsoft Teams is in use and Chats with people outside the organization are allowed, then we could use this as a communication channel.
The way data is send to the Command & Control Server is fully customized to fit into the environment. Adapting network traffic helps us to remain hidden in the general network noise while performing the attack simulation.
As part of our simulations we also perform data exfiltration of (randomized) datasets to discover if higher amounts of data can be exfiltrated out of the network, either in chunks or via a constant network stream.
Data Exfiltration describes the way we communicate with our Command & Control Server (TA0011). It also describes general data exfiltration out of the network, such as the goal (e.g. a dummy database) set in the assessment (TA0010).
Communication with the Command & Control server is done in various ways. This includes standard protocols such as HTTP and more bespoke protocols, if we identify that they are in use by our target. For example, if we identify that Microsoft Teams is in use and Chats with people outside the organization are allowed, then we could use this as a communication channel.
The way data is send to the Command & Control Server is fully customized to fit into the environment. Adapting network traffic helps us to remain hidden in the general network noise while performing the attack simulation.
As part of our simulations we also perform data exfiltration of (randomized) datasets to discover if higher amounts of data can be exfiltrated out of the network, either in chunks or via a constant network stream.
Impact
The Impact phase of the attack can be used in the attack simulation to proof that a pre-defined goal has been reached. Attackers may use it to manipulate, interrupt or destroy a system (TA0040). We usually do not disrupt any service and try to define an alternative goal to proof a specific level of access without performing the destructive action.
Alternative ways to proof destructive access rights are for example access to the Domain Administrator Account or high privilege access to heavily protected systems. If a destructive action like encrypting a file-system is selected, then we typically tend to do this on a reference system instead of the production system.
How often do you train your „lights-out“ protocol and data recovery?
| Example Technique | ATT&CK |
|---|---|
| Data Encrypted for Impact | T1486 |
Impact
How often do you train your „lights-out“ protocol and data recovery?
| Example Technique | ATT&CK |
|---|---|
| Data Encrypted for Impact | T1486 |
The Impact phase of the attack can be used in the attack simulation to proof that a pre-defined goal has been reached. Attackers may use it to manipulate, interrupt or destroy a system (TA0040). We usually do not disrupt any service and try to define an alternative goal to proof a specific level of access without performing the destructive action.
Alternative ways to proof destructive access rights are for example access to the Domain Administrator Account or high privilege access to heavily protected systems. If a destructive action like encrypting a file-system is selected, then we typically tend to do this on a reference system instead of the production system.
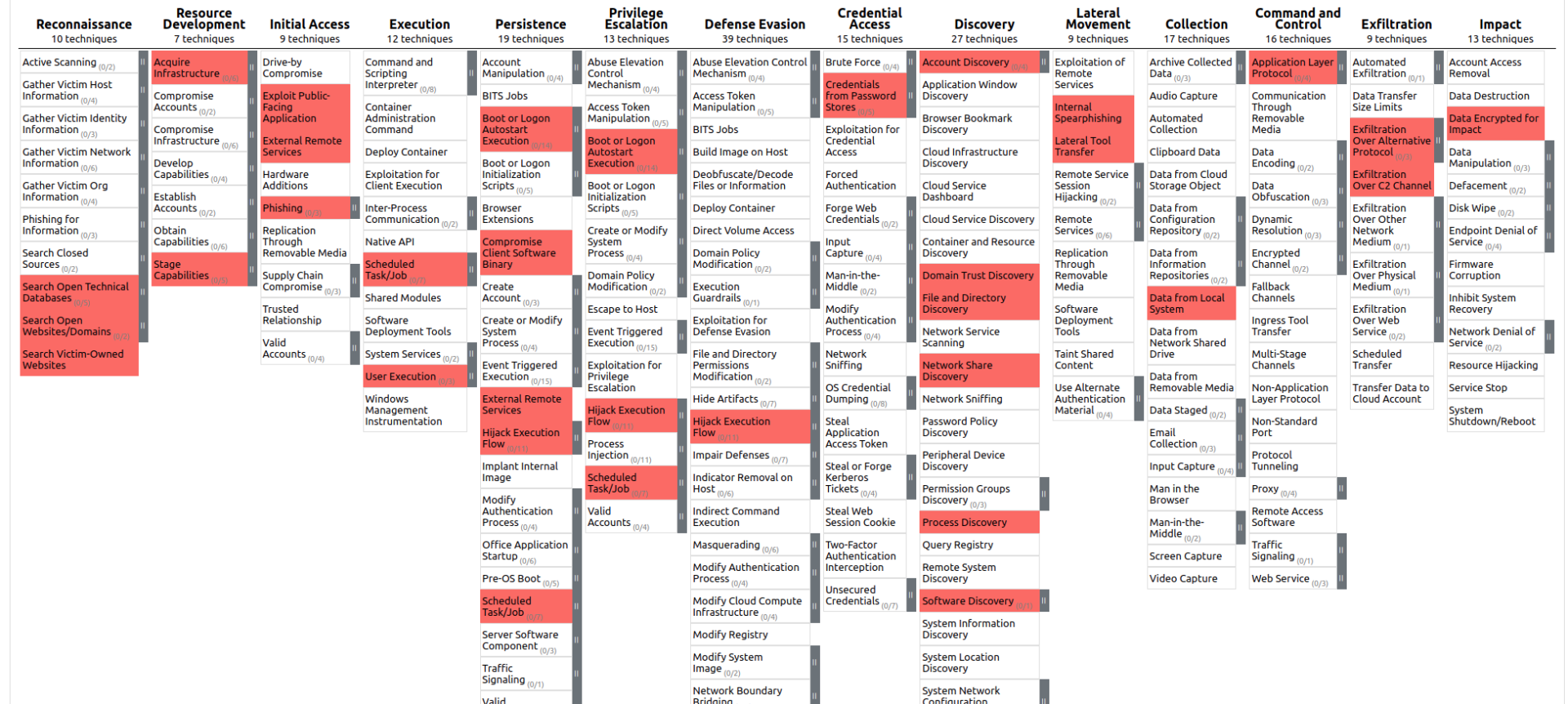
Attack Path Overview
The MITRE ATT&CK database holds 185 Techniques and over 367 Sub-techniques that can be used to describe an attack path. With the navigator it is also possible to create a more graphical version of the attacks we have mentioned in this post (highlighted in blue). This graphical version is also the initial step for remediation planning, before we describe more detailed information in our report. The full layer can also be viewed on our Y-Security GitHub (account):
Coming Next
Attack simulations should be more than just a technical verification of security controls and a list of vulnerabilities. With our transparent, dynamic and repeatable approach we enhance security controls and also change the mindset of the IT team. Working hand-in-hand with the team and giving them full insights into our actions and approach will help to start a long term transformation of your security.
In our second part we will have a deeper look into the different approaches to Attack Simulations and where the benefits of each are.
Stay tuned!
