Attack Simulations are known under a variety of names and variations like Red Team, Purple Team, Threat Simulation, Adversary Emulation or APT Simulation. They also exist as regulation driven schemes/frameworks like CBEST, GBEST, AASE, iCAST, TIBER. While the approach and focus may differ in some aspects, they all have one in common: Simulating a realistic Advanced Persistent Threat (APT) attack against an organization.
In our previous post we have introduced our general approach to Attack Simulations and placed the foundation for further posts. We introduced different players & teams, explained the cyber kill chain and different attack phases. Today, we continue the insights into our approach to Red Team exercises, Threat Simulation, and Bespoke Scenario Simulation. Additionally, we discuss the benefits and differences of each.
The Y-Security Attack Simulations Services
Our Attack Simulations service line (often known as Adversary Emulation) is structured into three main services including Red Team exercises, Threat Simulation and Bespoke Scenario Simulation. All three follow similar approaches, but have a different focus set which we will explain in the below. Each service includes a list (red circle) of typical phases we recommend, which can be adjusted where needed.
Red Team
Have you ever done a risk-controlled exercise with nearly no attack limitations on your assets?
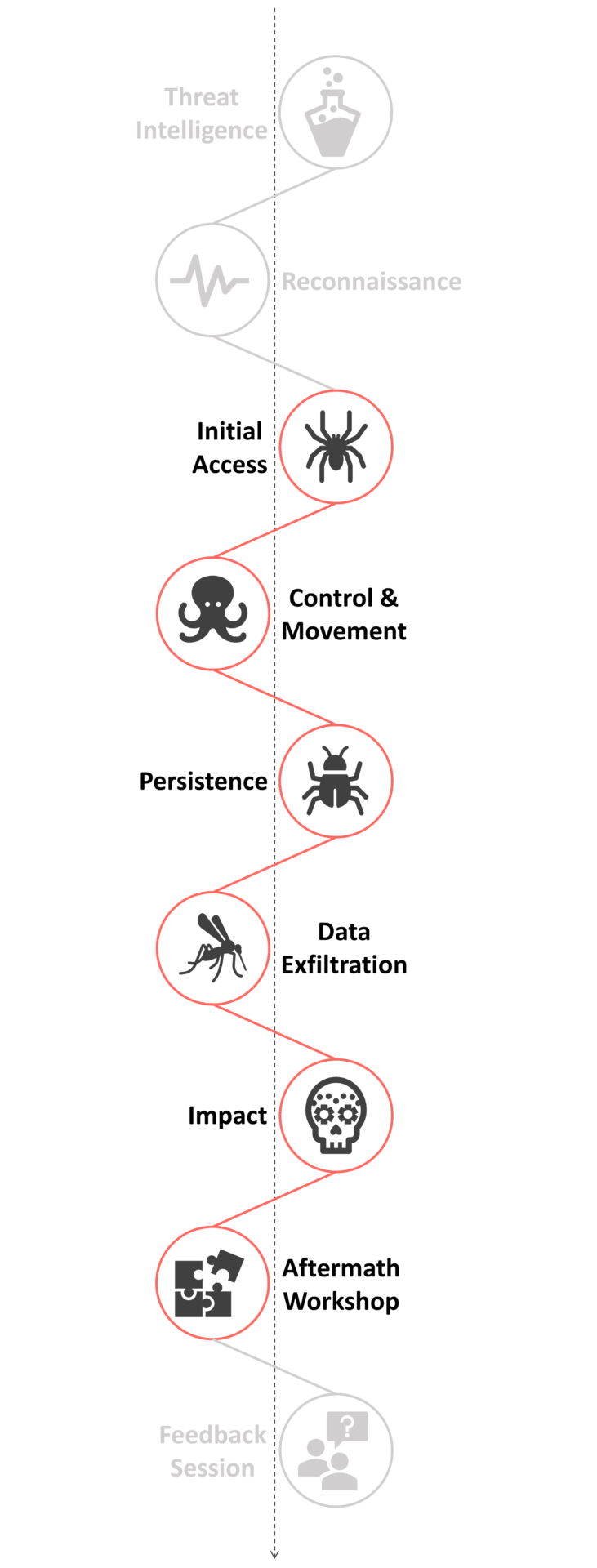
Exemplary Red Team Phases
What to expect from a Red Team
In our Red Team approach, we perform a full end-to-end exercise including all phases of the kill chain. This also includes Threat Intelligence in the beginning of the simulation and aftermath sessions with technical departments and the management.
During the Threat Intelligence phase, we identify the most likeliest threats an organization’s branch of industry faces and add customized threats on top. This phase also includes definition of the overall goal of the assessment which can for example be access to a Domain Administrator account or access to a specific server/network segment. A goal can also be physical access to a specific device or room in a premise. There aren’t limits on the goals of the simulation and they can also be broken down into smaller goals to identify the impact on a more granular level.
In Red Team simulations we are typically challenged by a Blue Team which is not aware that the simulation is running. The Blue Team is not a “must have” and we also performed exercises without our counterpart. The focus and benefit of the Red Team approach is that an organization gets full insights into real threats. This includes what can happen if they are under attack by an Advanced Persistent Threat (APT) group. Our aim is to be as sophisticated as possible and use the least risky attack path to reach our goal. We constantly evaluate risks associated with an action (attack) and discuss possible consequences with stakeholders before conducting them.
Our experience in TIBER and other simulations has shown that it is not always required to actively exploit vulnerabilities in software components. Often, logic issues exist in the network that can be exploited on our path to the defined goals. Those can vary from misconfigurations in the Active Directory or unrestricted access to file-shares and document server like SharePoint. It is also not unlikely that passwords are stored in spreadsheets or confidential keys are placed on a file-share.
We typically remain stealthy in the network for a a bit to learn about the environment (user behavior, tools user/admins use, reading documentation), plan the attack path and then perform the attack. Due to the complexity of chaining attacks together the time pertaining to launch an attack often takes longer than executing it. Especially, if multiple vulnerabilities/configuration issues need to be chained, to then launch the attack and reach our goal within minutes of executing it.
If the Red Team has not been discovered once reaching the goal, we perform the attack chains again with a lower sophistication level. This is usually done until we get spotted by the Blue Team. This approach does not only help to identify if escalation plans work as expected, but also helps to review the investigation process. If an attack was discovered, then compromised user accounts and systems should be reviewed in depth to re-create the attack chain.
After the simulation, we work with the Blue Team through the report and attack chain to strengthen detection capabilities. Additionally, we discuss the report with Senior Management to form an improved cyber security strategy.
Bespoke Scenario Simulation
New threats are always on the rise, how often do you train new attack vectors?
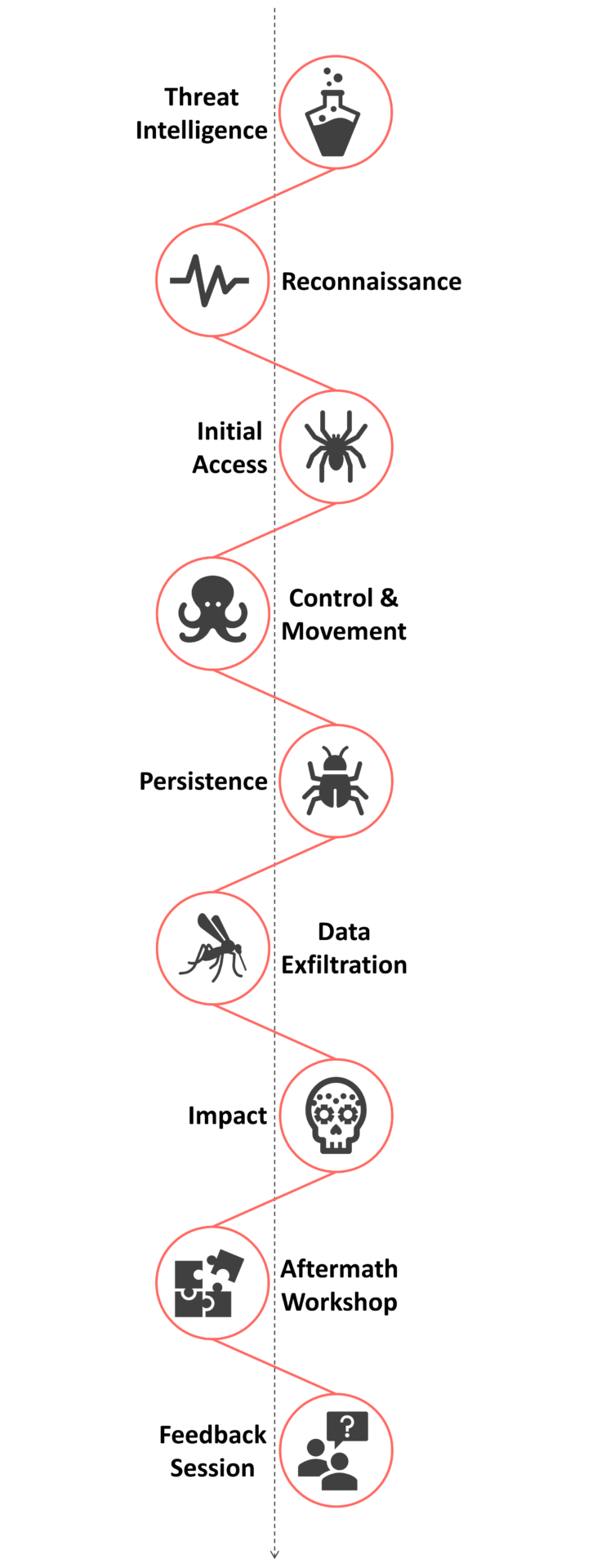
Exemplary “Malicious Employee“ Phases
Tailoring a Bespoke Scenario Simulation
Our experience in Penetration Tests and Red Team activities has been merged into the Bespoke Scenario Simulation approach. In this tailored approach we build attack scenarios including those that can be limited to: attack vectors, assets, or to a goal that should be reached.
We can limit the scenario to attack vectors like for example to Phishing attacks. In this simulation we identify how many employees have clicked a Phishing URL or interacted with our Phishing page.
If the target is the external Infrastructure, then we can for example define ‘access to the customer database’ as a goal. In this style of attack the scope of included assets is typically kept wide, but can also be limited if only a specific region should be targeted.
Purple Teaming & Playbook Attacks
Working hand-in-hand with the Blue Team as part of Purple Teaming or Playbook exercises is another tailored approach we can take. We use this approach to perform chosen attacks on different sophistication level to reach a pre-defined goal. The simulation is fully tailored and does not necessarily include all phases of the attack chain. Focus is on simulating attacks without necessarily trying to remain undetected from the Blue Team as we work closely with them.
If the simulation should be done in a Playbook style attack, then selected attacks and threats are tailored. They can be as simple as: Attacking Windows Print Spooler, Attacking your Exchange Server, Kerberoasting, collecting Active Directory information or more sophisticated attacks like placing a backdoor in systems and applications.
Malicious Employee & Stolen Laptop Scenario
Our team has lots of experience in performing tailored attacks. Example scenarios our team has performed include: “Malicious Employee” in which we breached the Active Directory from the perspective of a standard employee. This scenario included Local Privilege Escalation and moving within the Active Directory to compromise Domain Administrator accounts.
During a “Stolen Laptop” scenario we look into a laptop’s physical security, access possibilities without authentication credentials and backdoor possibilities.
Physical Attacks
Digital attacks are just one way to breach into an organization. Another way can also be physical attacks against premises and planting malicious devices in networks and restricted zones. Dressing up as a technician and asking for entrance at the front desk is just one of the options and ways to get inside premises.
>Equally to our other exercises we map our actions to Techniques and verify them with the Blue Team during and after the assessment. The presented report also includes step-by-step instructions to repeat performed attacks.
Benefits of executing Attack Simulations
Attack Simulations services follow a similar approach and we have shown the differences in the above post. Each of the approaches have their very own benefits next to the general benefits of an Attack Simulation. In general they help to verify the resistance of an organization against a targeted cyber attack and provide a real-world attack training for a Blue Team.
The Red Team approach can be seen as the attack with the highest sophistication level as we build a unique attack plan and actively bypass security controls. With Threat Simulation we perform actions of a specific APT groups and software they use on the lowest risk level possible and verify the resistance of a single Threat. The Bespoke Scenario Simulation is our “pick and simulate” way to provide the most targeted and tailored attack plan to train the team where it is needed most.
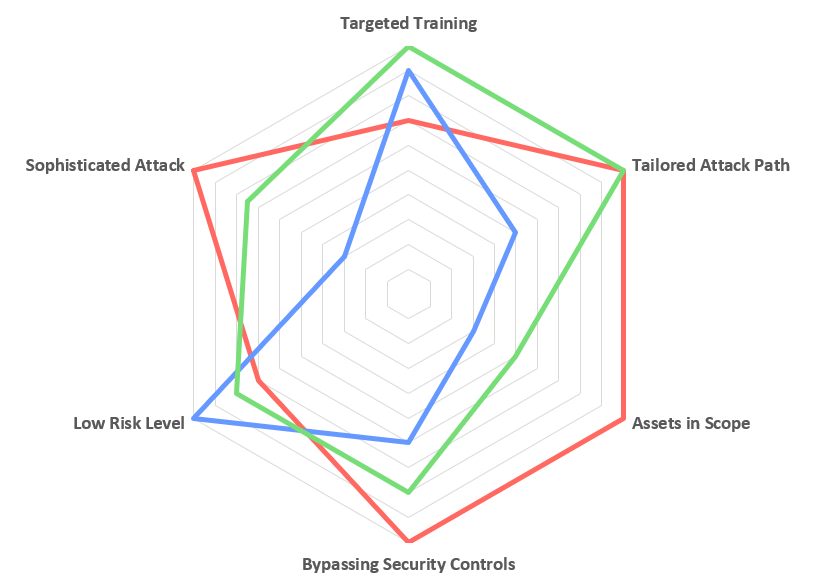
The below diagram shows the different approaches in relation to each other. It should be noted that especially for the Bespoke Scenario Simulation, the diagram varies per scenario.
Red Team
Threat Simulation
Bespoke Scenario
The below table describes each category of the diagram in more detail. As before, the focus of a simulation varies and other categories can be in focus.
|
|
|
|
|
|---|---|---|---|
| Category/Service | Red Team | Threat Simulation | Bespoke Scenario |
| Tailored Attack Path | Fully tailored and customized to the environment | Pre-defined by the group or software to be simulated | Customized to scenario |
| Assets in Scope | Full attack surface of an organization | Limited to specific assets | Varies between full attack surface, or limited assets like network regions and single systems |
| Sophisticated Attack | Highest sophistication level | Sophistication depends on the simulated threat | Varies between highest sophistication and intended lower sophistication |
| Low Risk Level | Production environment, using our risk-based approach. Attacks are discussed prior execution | Performed in a test/production environment, using our risk-based approach. Attacks are discussed prior execution | Performed in a test/production environment, using our risk-based approach. Attacks are discussed prior execution |
| Bypassing Security Controls | Bypassing security controls is one of the key focus points to reach the goal of the assessment | Bypassing security controls depends on the simulated threat | Depends on performed scenario. Can be key focus point in Purple Team exercises |
| Targeted Training | Aftermath workshop with the Blue Team to walk through detection controls and used attack chain | Aftermath workshop with the Blue Team to walk through TTPs of the simulated group/software and where detection controls did not work as expected | Interactive training opportunity while working hand-in-hand with the Blue Team |
Attack Simulations are a complex topic and different approaches exist to perform them. Even though the focus and depth varies, they all have one in common – being a realistic end-to-end Advanced Persistent Threat (APT) attack against an organization. Finding the best approach is not an easy topic. With a Red Team approach one can assure the highest sophistication level when attacking the full surface of an organization. The Threat simulation limits the attack surface, but allows a more defined attack pattern to be used and provides explicit Threat training for the defending team. The Bespoke Scenario is the best when a smaller subset of the kill chain needs to be validated explicitly.
Coming Next: Running a Threat Intelligence Based Ethical Red Teaming (TIBER) assessment
With this and the previous post we have completed the basics of Attack Simulations. In our next posts we will give insights into how we run a Threat Intelligence Based Ethical Red Teaming (TIBER) engagement, APT software simulation and our general approaches for Penetration Tests and Security Trainings.