TIBER is an acronym for Threat Intelligence-Based Ethical Red-Teaming. TIBER is a framework for adversary emulations and attack simulations that has been released by the European Central Bank ECB in 2018. The central bank of each European country can adopt the standard – for example, the Deutsche Bundesbank and the Bundesministerium der Finanzen BMF released the framework for TIBER Deutschland (TIBER-DE) in summer 2019.
If not stated otherwise we are referring to the TIBER-EU framework. National implementation might differ.
The TIBER-EU framework is not exclusive for the core financial entities, but can be used by everyone interested across the financial and other sectors. The idea is to provide resilience against sophisticated targeted cyber attacks.
The TIBER-DE framework targets large banks, large insurance companies, the financial market infrastructure and IT service provider that are critical for the financial market in Germany.
TIBER-EU is a common framework that delivers a controlled, bespoke, intelligence led red team test of entities’ critical live production systems. Intelligence-led red team tests mimic the tactics, techniques and procedures (TTPs) of real-life threat actors who, on the basis of threat intelligence, are perceived as posing a genuine threat to entities. An intelligence-led red team test involves the use of a variety of techniques to simulate an attack on an entity’s critical functions (CFs) and underlying systems (i.e. its people, processes and technologies). It helps an entity to assess its protection, detection and response capabilities.
ecb.tiber_eu_framework.en.pdf – Section 1.1 “What is TIBER-EU?”

The TIBER core objectives
In TIBER we have identified knowledge sharing as one of the most important parts of the engagement over all phases. The TIBER players can be split in the TIBER Cyber Team, White Team, Threat Intelligence Team and Red Team. Working with so many different key members can be challenging and a TIBER assessment can only be successful when all stakeholders work closely together, in the spirit of trust and cooperation.
We have visualized the relationship as follows to summarize the setup between the teams involved in a TIBER engagement:
The Players
The TIBER Cyber Team
TIBER engagements are assessments typically overseen by the TIBER Cyber Team and are under the control of the White Team.
The TIBER Cyber Team (TCT) supports the entity so that the test is performed in an uniform and controlled manner. Their oversight is an important part of when performing a test on critical live production systems.
The White Team
The White Team is responsible for the assessment and it ensures that information are processed at the right time for each of the teams. This is important in order to ensure the simulation is effective and worthwhile. The team acts as a planning group and is usually formed out of individuals of the institution that gets tested. People in the team are working in key positions who are consulted if a serious incident is reported.
Threat Intelligence Team
Threat Intelligence is required right at the start of the engagement to identify potential threat actors. The provider should use multiple sources of intelligence to generate a report that is shared with the Red Team. This is to ensure that the Red Team can develop the attack chain and scenarios in conjunction with the Threat Intelligence provider.
Red Team – The Attacker
The Red Team provider (for example Y-Security) plans and executes the simulation. The Red Team will review identified threats outlined by the Threat Intelligence Team and expand them where required to form attack scenarios. The threat scenarios are based on various TTPs used by sophisticated attacker groups.
Blue Team – The Defender
The Blue Team plays a crucial part in the TIBER engagement – however, it is important to not share information about the TIBER project while it is still in the testing phase. The Blue Team will get involved latest in the closure phase of the assessment. Members of the Blue Team will participate in the replay and follow-up sessions.
Red Team vs TIBER vs Penetration Tests
You may be new to the game of Attack Simulations, but you might have come across Penetration Tests. Let’s quickly jump into the differences and advantages of each:
A Penetration Test follows the goal of understanding the security exposure of a defined system, application or network. In a Penetration Test access to user credentials, source code and similar is usually provided to ensure the best outcome. This also includes disabling any Intrusion Prevention System. The penetration tester will ensure to report and rate every security issue that affects and could affect the systems in scope. This is great and you will be able to make an educated decision afterwards what the associated risk is.
A Red Team engagement is a goal-based assessment with the challenge to find an attack chain that allows reaching the defined goal. The Red Team will perform the assessment from almost zero-knowledge and follow typical behavior of real threat actors. This helps to understand the countermeasures in place and what level of complexity is required to bypass them. The engagement does not focus on a specific vulnerability, but aims at finding the most efficient way through the network to the defined goal. This is perfect to explore end-to-end attack chains and understand the big picture of your company’s security exposure.
Only when risk controlled; It is safe(r) to execute
A key means of managing the risks associated with the TIBER-EU test is to use the most competent, qualified and skilled TI and RT providers with the requisite experience to conduct such tests.
ecb.tiber_eu_framework.en.pdf – Section 6.3 “Minimum requirements for providers”
Risk management is always a balancing act in the offensive security world. It is even more important to define clear scopes and boundaries and define the liability and escalation paths. In our experience the TIBER test is running much more to everyone’s needs, the better the risk management is defined.
The Threat Intelligence and Red Team provider of course need to meet the security and the confidentiality requirements, including detailed data destruction and breach measurements in place. Furthermore, a defined list of actions not allowed, like destruction of equipment and uncontrolled modification of data/programs must be provided by the White Team.
As an advance readiness check the White team needs to ensure that every in-scope system has a sufficient backup and restoration capabilities in place.
All executions of the Red Team need to be documented and timestamped. This is not only an important part for a meaningful report and a successful feedback session. It is even more important in the risk assessment to ensure everyone (involved) knows at any time what actions have been performed. This also allows the White Team to differentiate between real world attacks successfully discovered by the Blue Team and attacks performed under the TIBER umbrella.
There are three phases of a TIBER engagement
TIBER defines three phases that are divided into: Preparation, Testing, Closure.
Each phase has its own important aspects even if the real assessment is only performed within the Testing phase. We will now investigate every phase to understand for each:
- The requirements for the phase
- The teams involved
- The outcomes
What you need to prepare for in a TIBER
The preparation phase describes the formal launch of the TIBER engagement and will last for approximately 4-6 weeks. During that time the TIBER Cyber Team (TCT) is getting involved and the procurement process starts. We won’t go into the details of the procurement here, but there is a procurement guide available from the ECB that holds all relevant information.
The TIBER Test Project Plan should be made available to all stakeholders by the White Team. The plan should include the timeline and schedule for meetings between the entity, the Threat Intelligence / Red Team providers, and the TIBER Cyber Team.
Given the sensitive nature of the tests, and the potentially detailed findings on the weaknesses and vulnerabilities of specific entities, all stakeholders must use code names for the entities being tested
ecb.tiber_eu_framework.en.pdf – Section 6.8 “Use of code names”
The following animation will support with the work flow in the preparation phase and shows the meetings and documents that need to be created at each milestone of the engagement:
The White Team invites to a first meeting which is the official launch of the TIBER engagement for all of the stakeholders of the project.
One of the most important parts of the preparation phase is the scoping where the entity (and authorities) needs to agree to the scope of the test. The Critical Functions (CF) should be included, but if required Non-Critical Functions can be part of the scope, too. CF are not a system; it is a function. The framework describes Critical Functions as:
The formal TIBER Scope Specification document should be completed in the scoping process and agreed on. Before completing the document, it is highly recommended to request input from the Threat Intelligence and Red Team providers, if the procurement for them has been completed already. Furthermore, the ECB recommends board level approval for the defined scope. The scope specification document helps mapping the Critical Functions to systems and privileges in the network allowing to define the goals and flags for the Red Team.
The people, processes and technologies required by the entity to deliver a core service which, if disrupted, could have a detrimental impact on financial stability, the entity’s safety and soundness, the entity’s customer base or the entity’s market conduct.
ecb.tiber_eu_framework.en.pdf – Section 7.5 “Scoping”
The TIBER Testing phase
The testing phase concludes out of two major phases, one being the Threat Intelligence phase, while the other one is the Red Team testing phase. The following video provides an overview on the meetings and documents required for each milestone of the project:
First, TIBER needs some Threat Intelligence
Threat Intelligence based scenarios are required to mimic real-world adversaries. To create those scenarios, two complementary tools are used: the Generic Threat Landscape (GTL) Report and the Targeted Threat Intelligence (TTI) Report.
Generic Threat Landscape & Targeted Threat Intelligence
Threat intelligence plays a key role for any TIBER test. The framework requires a Targeted Threat Intelligence Report, which sets out the specific threat scenarios. However, before this is created an optional element can be fulfilled by creating a Generic Threat Landscape (GTL) assessment which includes an overview of the national financial sector. So, the GTL complements the TTI Report which will be used to suggest scenarios. When national agencies get involved the GTL report is the right place to provide feedback.
For TIBER-DE the GTL report will be provided by the Bundesbank
The Red Team will be involved at the very end of the TTI Report generation when the scenarios are mapped to the Red Team Test Plan. It should be noted, that by nature the entities Critical Functions (CF) usually sit within the internal network and hence the intelligence towards those is always limited for an external provider. To support with that challenge, it is expected that the Critical Functions, a threat assessment or register and examples of recent attacks are provided as input to the provider.
In TIBER-DE a threat assessment is not part of the process.
Target and Threat identification
The provided information will be used and separated into Critical Functions to identify potential attack surface (target) and to identify relevant threat actors (threat).
The target and threat identification is a core element of the process. The Threat Intelligence provider carries out an exercise, just like real world attacker would do, to gain a picture of the weak points of the entity that is tested. For threats it is important to present a credible picture of the cyber threat landscape and to catch the right real world threat actors that should be incorporated with their TTPs in the Red Team testing.
Targeted Threat Intelligence Report
The results from the target and threat identification result into the Targeted Threat Intelligence Report. National agencies can provide feedback to the report. To complete that report the Threat Intelligence Team and the Red Team will collaborate to create tailored and realistic tailored attack scenarios.
Closure of the Threat Intelligence phase
At the end of the Threat Intelligence phase a workshop is conducted in which the report is presented, summarized and feedback is gathered. This workshop is also a milestone in the project management as it indicates the handover to the Red Team who will present a first Red Team Test Plan. The Red Team Test Plan includes:
The Red Team
The end of the Threat Intelligence phase and the start of the Red Team phase go hand-in-hand and the Red Team takes the lead of the testing for the TIBER engagement. The TIBER-EU framework implementation guideline estimates 10-12 weeks of effort for this phase. However, the time required heavily depends on the scenarios that have been taken to reach the Critical Functions and the associated flags. The time required could be less, but it should be monitored that the time is sufficient – otherwise it can be required to take a leg-up too early in the process.
The test will not result in a pass or fail, but will provide all parties with an insight into strengths and weaknesses, and enable the entity to learn and evolve to a higher level of cyber maturity.
ecb.tiber_eu_framework.en.pdf – Section 1.4 “Who are the key stakeholders involved in the adoption and implementation of TIBER-EU tests?”
Methodology used for the Y-Security TIBER testing
The testing methodology is bound to the cyber kill chain. At Y-Security we are forming our kill-chain out of two known frameworks. It includes the Lockheed Martin kill-chain and the MITRE ATT&CK® framework. We have written about the phases in our previous posts Insights Into Attack Simulations – Part 1 and Insights Into Attack Simulations – Part 2.
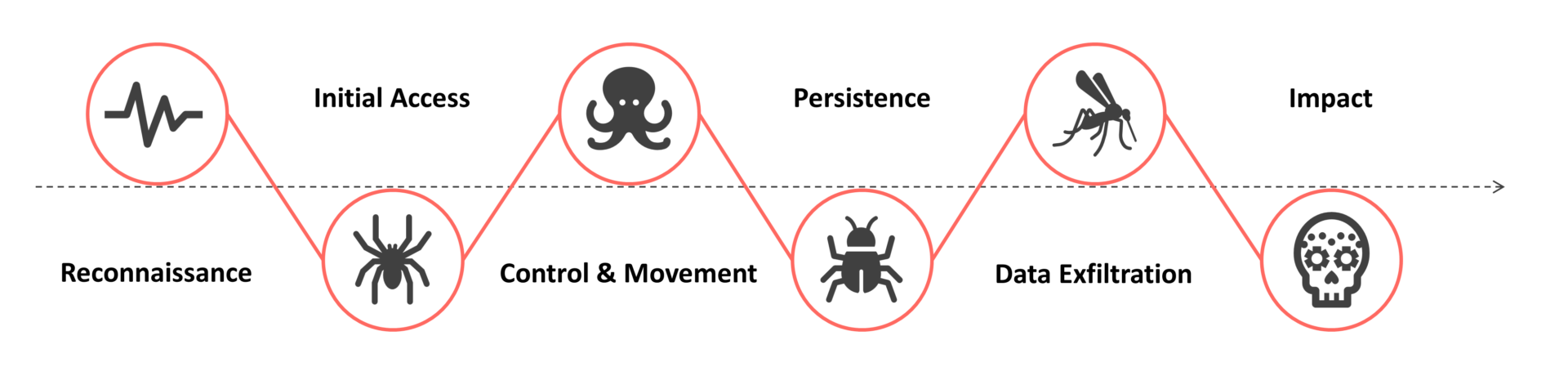
The elements in the Y-Killchain can occur in multiple TIBER killchain elements. If you want any more details – we already have described the Y-killchain in our previous post.
Creating a Red Team Test Plan and realistic Attack Scenarios
The Red Team Test Plan and the Attack Scenarios planning are important milestones in the TIBER engagement. On the right you can see what should be included in the Red Team Test Plan as an absolute minimum. The Red Team sets milestones within the Test Plan to ensure attack scenarios are simulated in the time available. A leg-up should have been defined in case the team runs out of time; to provide an option to move to the next stage. However, leg-ups are always dangerous as they are often easier to spot for the Blue Team and it is difficult to provide a realistic environment to land in. Anyways, it is an important part of the Red Team that should have been planned in case it is required.
The attack scenarios are defined by the Threat Intelligence team and get finalized by the Red Team. It is up to the Red Team to provide creative solutions when facing heavy mitigation and protections in the entity network. To make the attack as realistic as possible, multiple attack ways for a flag should exist and the TTPs to reach them should be taken from known threat actors, but must be extended with own and custom TTPs where possible.
- Critical Functions and how they can be mapped to the scenarios
- Defined goals and flags
- Leg-ups (used in case an element of the Red Team scenario cannot be reached within the provided timescale)
- Risk mitigation steps
- Escalation procedures
- Test & Report delivery dates
While the idea is to create realistic scenarios mimicking possible future attacks and show threats from real-word actors – those usually can take many months to prepare an attack. If feasible and agreed by the involved teams some information can be released to the RT including information on the people, processes and systems targeted.
The execution of the test
One of the key parts of a TIBER engagement is to progress stealthy. Under any circumstances, the RT does not want to get caught by the Blue Team. If for example the implant of a Red Team gets discovered by the Blue Team, then there should be a backup plan for other implants in the network to remain intact. This is not always possible and dangerous to perform in order to not breach the new implant and infrastructure. Various techniques and variants exist, but each has its own drawbacks.
Another key element is to maintain the available time and milestones. The Red Team can be technically brilliant and very creative, but if the teams run out of time, there is no way to proof the resilience of the entity – hence it is important to have regular catchups with the White Team and inform everyone of the progress and actions planned for the next steps.
As for any Red Team, the actions performed by the Red Team must be extensively logged. This will be required for the reporting and the replay with the Blue Team.
Wrapping up and the closure phase of TIBER
In the closure phase all stakeholder can reminisce on the outcome of the test. The phase includes the remediation planning and result sharing:
Red Team Test Report and Blue Team Report
Generating the Red Team Test Report is a time-consuming task and shouldn’t be underestimated – a draft should be completed within two weeks of the last day of testing. We do create a single report, but we also split the document in multiple parts to allow easier reading and to target the relevant audience. The report will be provided to the entity which provides the document to the TIBER Cyber team, too.
At the same time the key members of the Blue Team can be informed about the simulation that has been performed in the past month. The Blue Team will use the Red Team draft report as a basis to generate a Blue Team report. Here, it can be seen that a key element is to provide a very accurate, timestamped report about the actions performed. The Blue Team report should map its observations alongside the Red Team actions, and it should be completed prior the replay workshop.
The big aftermath – Workshops
Red Team and Blue Team replay
TIBER is all about the learning experience and hence the replay workshop is designed to learn from each other. The steps taken by the Red Team are replayed and reviewed by the Blue Team. If needed, then an interactive Purple Teaming element can be added to better understand how the attack could have been responded to.
360-degree feedback
The feedback session will be hold between the entity, the TIBER Cyber Team, the Red Team and the Threat Intelligence team with the goal of reviewing the experience made during the engagement.
Remediation Plan and Test Summary Report
As a closure to the TIBER test the entity should draft a Remediation Plan and Test Summary Report. The report needs to be based on the test results and provide improvement and mitigation comments to the vulnerabilities identified.
Y-Security Conclusion on TIBER
There are variances to the above example – for example intelligence agencies and other parties could be involved if this is beneficial for the project outcome. However, in our experience of TIBER tests that usually isn’t the case and the case described in this blog post is a typical TIBER engagement.
TIBER is a fantastic instrument to test the resilience in an open, but risk-controlled environment. The ethics and standards of TIBER will support organizations to be a step ahead in the game.
Update 15. September 2021
We have received feedback to our TIBER post. In particular, we have received feedback about the differences between the TIBER-DE and the TIBER-EU framework. We have clarified this in the text where needed by adding TIBER-DE comments to the text.
However, it should be noted that our post is based on the TIBER-EU framework. Assumptions for national TIBER implementation might differ. We would like to thank the reviewer for reaching out to us and working with us on the updated version.
The following summarizes the changes we have made:
- Clarified that TIBER-EU is the main focus in this post and that national implementation might be different
- Specified the target audience for TIBER-DE & TIBER-EU assessments
- Referenced Videos to TIBER-DE
- Added clarification about timing of the Red Team phase
- Added that Agencies can provide feedback to the TTI Report
- Clarified that a threat assessment or register is not required for TIBER-DE
- Removed the terms “Regulator Team” and “TIBER simulation”
- Added clarification about TIBER regulation
- Enhanced “The TIBER Cyber Team” and “The White Team” definition
