TIM BPM Suite / TIM FLOW – Multiple Vulnerabilities
Y-Security discovered multiple vulnerabilities affecting the TIM BPM Suite / TIM FLOW software by TIM…
Out of Office Assistant – Cross-Site Scripting (CVE-2025-45938)
Golive – Server-Side Request Forgery (CVE-2025-45939)
AXESS Auto Configuration Server – Denial of Service (CVE-2024-56316)
StealthGuardian – Automatic TTP Analysis
This August we publicly released one of our internal tools, StealthGuardian, at Black Hat USA…
Black Hat USA 2024
The Y-Security team will be at the Black Hat ARSENAL USA 2024 on the 7th…
Red Team Ops I & II Review
From Concept to Creation: Checking The Security Of LoRaWAN Implementations
Mobile Application Testing on Apple Silicon
EasyMind – Cross-Site Scripting (CVE-2023-30452)
Reminder for Jira – Cross-Site Scripting (CVE-2023-30453)
Advantages of Cloud Audit and Cloud Penetration Testing
Offensive Security assessments in cloud environments can be performed in many ways. Today, we discuss…
Hack The Box BlackSky Cloud Hacking Labs – Blizzard
Hack The Box BlackSky Cloud Hacking Labs – Cyclone
Hack The Box BlackSky Cloud Hacking Labs – Hailstorm
German OWASP Day 2023
Y-Security is sponsoring the German OWASP Day 2023 (#GOD). The Y-Security team will be at…
Ynachten 2022
“Die größten Ereignisse, das sind nicht unsere lautesten, sondern unsere stillsten Stunden.” Friedrich Wilhelm Nietzsche…
Risk Management – Better Safe Than Sorry
Welcome To The Team – Thore
The Scatter Swine
Let’s review attacks of the last weeks (well, months …) against users of a well-known…
Year-One-Ylights
Y-Security becomes One Year old – let’s celebrate! In July 2021 we’ve announced the launch…
TIBER in a Nutshell
The Y-Security service lines are divided into Attack Simulations, Penetration Tests and Security Trainings. Below…
Insights into Penetration Test & Attack Simulation Reports
Writing a technical good report is just one key aim when it comes to formalizing…
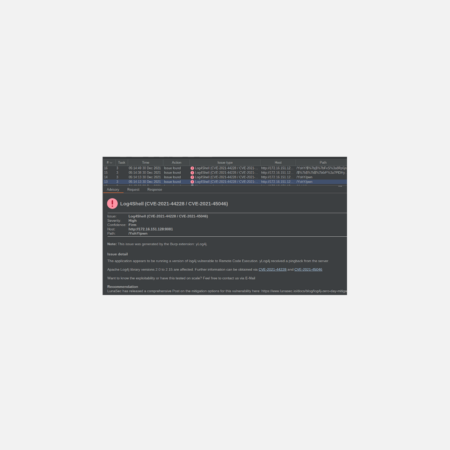
Blind Detection of the Log4j vulnerability en scale
A lot has been said during our self-imposed 30 days embargo of our detection plugin…
Looking at the Portswigger Burp Suite Certification
Y-Security recently took the challenge of mastering the Burp Suite Certification offered by the creators…
Microsoft Azure Portal – CSV Injection
Microsoft Teams – CSV Injection
Threat Simulation – Mimicking an APT
Most have already heard about ransomware attacks, either in the news or as they have…
Microsoft Azure Portal – Persistent Cross-Site Scripting
All You Need To Know About Threat Intelligence-Based Ethical Red-Teaming
TIBER is an acronym for Threat Intelligence-Based Ethical Red-Teaming. TIBER is a framework for adversary…
Insights Into Attack Simulations – Part 2
Attack Simulations are known under a variety of names and variations like Red Team, Purple…
Insights Into Attack Simulations – Part 1
Disclosure Policy
Y-Security – That’s us
At Y-Security we are specialized in performing Attack Simulations exercises, highly complex Penetration Tests and…